According to Cisco’s annual cyber security report, cyber criminals attempt to obtain trustworthy data from unsuspecting Internet users every second with the help of approximately 3,000 manipulated sender addresses. Learn more about phishing in our blog-post.

| What is phishing? Phishing is a combination of the words “password”, “harvesting” and “fishing”. Phishing is a technique used to obtain confidential data from unsuspecting Internet users. The affected victim loses double, data and money! |
A phishing attack usually starts with an email asking you to reveal confidential data. A phishing email may make an enticing offer or demand immediate action.
In most cases, you will receive a link that leads to a fake website where you can enter confidential data, such as:
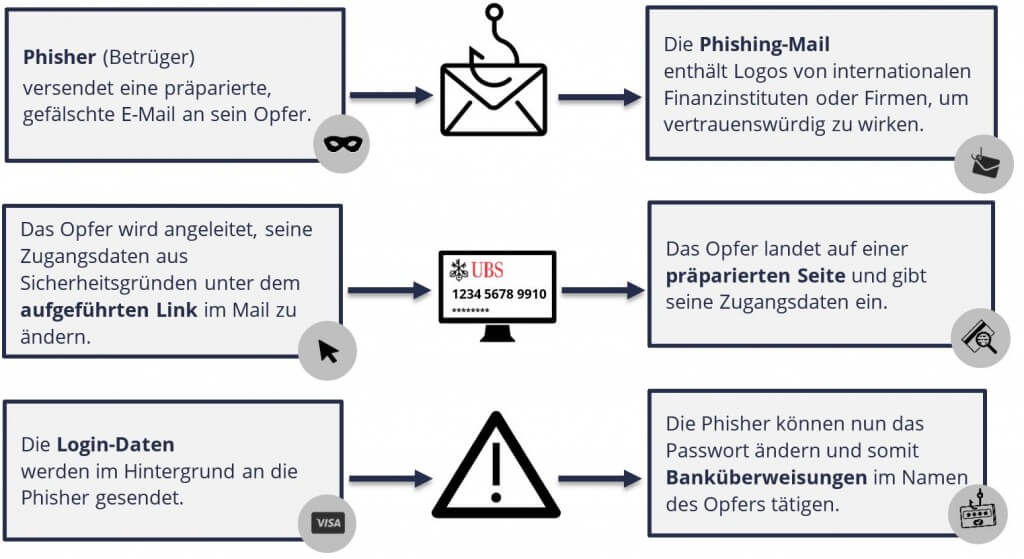
To avoid becoming a victim of phishing, look out for these typical characteristics:

Don’t worry – something like this can happen.
Here’s how to react correctly in such a situation:

You can find more information on the topic of “phishing” in our accompanying handout.